If you need to analyze and report on Microsoft Forefront Threat Management Gateway log files, the most common stumbling block is enabling access to the default SQL Express databases that contains the firewall and web proxy log files.
The log databases are stored in an SQL Express instance named MSFW. By default these databases cannot be accessed by a remote computer. I’d first like to say that we recommend changing TMG’s logging to W3C text files, as these logs are about 5-6 times faster to import, and you don’t need to worry about the steps below.
But if you need to stick with the SQL Express logging, here are the basic steps to enable access to the logs from a remote computer:
Enable TCP access to the MSFW instance
To do this:
- Log into your Forefront TMG server using administrator credentials.
- Select Start | All Programs | Microsoft SQL Server 2008 | Configuration Tools | SQL Server Configuration Manager.
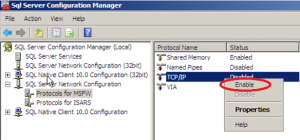
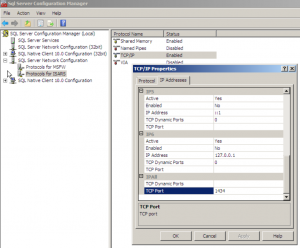
- Expand SQL Server Network Configuration and select Protocols for MSFW
- Right-click TCP/IP and select Enable
- Click OK on the Warning dialog informing you that “changes will not take effect until the service is stopped and restarted.”
Set the listening Port on the MSFW instance
Once TCP/IP is enabled on the MSFW instance, you need to set it to listen on port 1433
- Select Protocols for MSFW under SQL Server Network Configuration
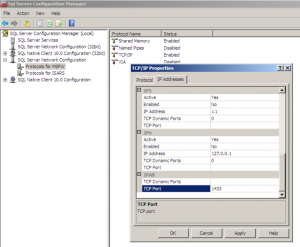
- Right-click TCP/IP and select Properties.
- Click the IP Addresses tab and scroll to the IPAll section at the bottom of the list.
- Change the TCP Port to 1433 and ensure nothing is entered in TCP Dynamic Ports (Delete the ‘0’ value if present). Click OK and click OK on the Warning dialog.
Change the listening port on the ISARS instance
The ISARS SQL instance also listens on port 1433 and this can cause connection issues. Change this instance to use port 1434:
- Still in SQL Server Configuration Manager, select Protocols for ISARS under SQL Server Network Configuration
- Right-click TCP/IP and select Properties.
- Click the IP Addresses tab and scroll to the IPAll section at the bottom of the list.
- Change the TCP Port to 1434 and ensure nothing is entered in TCP Dynamic Ports. Click OK and click OK on the Warning dialog.
Restart the Services
For the above changes to take effect, you need to restart the SQL Server (ISARS) and then the SQL Server (MSFW) services in that order.
- Go to Start | Administrative Tools | Services
- Right-click the SQL Server (ISARS) service and select Restart.
- Right-click the SQL Server (MSFW) service and select Restart.
Test the connection from the WebSpy machine
You should now be able to connect to the MSFW databases from a remote computer. To test the connection, we recommend that you install SQL Management Studio on the machine running WebSpy and try to connect to <TMGservername>\MSFW, 1433 (replace <TMGservername> with your actual server name or IP address). For example TMGServer\MSFW, 1433 or 192.168.0.10\MSFW, 1433.
As long as you are logged into Windows with a user account that is a local administrator on the TMG server, you should be able to connect without issue.
Importing the TMG Log files into WebSpy Vantage
Once you have established a connection, you can import your logs using WebSpy Vantage like so:
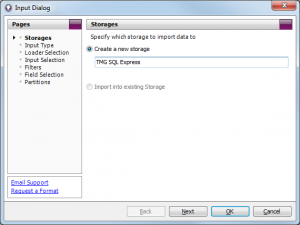
Create a new Storage
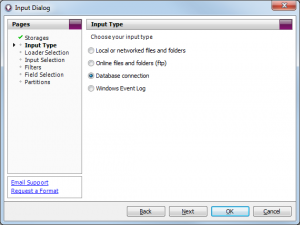
Select Database Connection
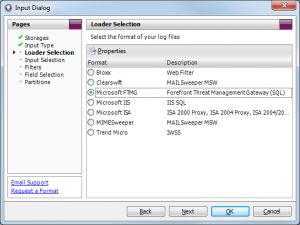
Select the Microsoft FTMG Loader
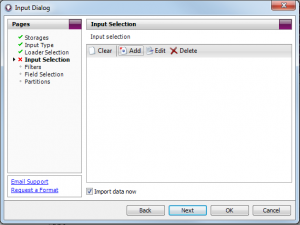
Click Add
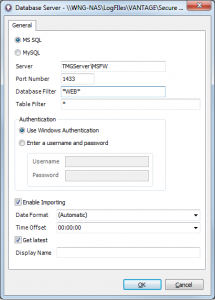
Enter TMGServer\MSFW and port 1433
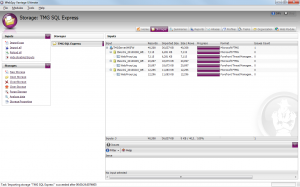
Successfully Imported WebProxy Logs
The screenshots above also illustrate using a database mask of *WEB* to only import the WebProxy logs. If you only want to import the Firewall logs, set the database mask to *FWS*. If you want to import both the WebProxy and Firewall logs, leave the database and table masks set to *.
Now that you have your log files imported, you can run a quick ad-hoc analysis on the Summaries screen or generate any of Vantage’s default web of firewall reports. M
Make sure you also download our Forefront TMG specific Aliases and report template. For more information, see our Forefront TMG How To page.
If you have any questions or encounter any hurdles, please leave a comment below.

[…] If you need to analyze and report on Microsoft Forefront Threat Management Gateway log files, the most common stumbling block is enabling access to the default SQL … more… […]