Majority of our social networking tips and ‘How to’ articles are aimed at organizations managing and reporting on network traffic to improve online safety at work.
This time around I thought I share some tips focusing on how individuals can ensure they’re being smart and safe when engaging in social networking activities. Hopefully these tips can assist you, or the people working in your organization, in avoiding being exposed to the dark side of social networking where hackers, identity thieves, fraudsters and stalkers are lurking in the shadows.
I’ve picked five tips I thought were quite helpful and perhaps not as obvious as not sharing personal information such as birth date and address, keeping passwords safe, be selective whose friendship requests you accept, use appropriate virus/phishing software etc.
1. Limit work history details on LinkedIn
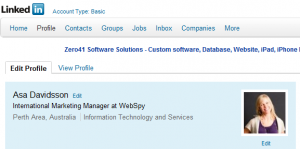 Although tempting, it is not advisable to use LinkedIn as an online resume displaying all information about time and place with previous employers and educational institutions.
Although tempting, it is not advisable to use LinkedIn as an online resume displaying all information about time and place with previous employers and educational institutions.
Too much personal information publicly available simply makes it too easy for identity thieves to use the information to fill out loan applications or guess password security questions. A hacker recently used social reverse engineering to find information, such as post code, home town, high school graduated from etc, in order to hack into VP candidate Sarah Palin’s web mail account.
If you really feel the detailed information will help you when looking for a new job then expand the details during the job hunting process and cut back later after you have a position.
LinkedIn also offers some capabilities to restrict information. You can close off access by others to your network of contacts, something you don’t have to share if you don’t want. This is a common practice by sales professionals and recruiters not wanting to expose their valuable network to others who might poach customers or prospects from them.
2. Avoid sharing location information
Hopefully you’re already aware that sharing phone and address details online is a very bad idea. You might also think twice before posting “Away for the weekend…returning on Monday” on public sites like Twitter and LinkedIn, to avoid attracting attention from potential stalkers or burglars.
What you might not have considered is that, over time, seemingly innocent and non-specific information can be pieced together, giving lurkers a much more complete and rich picture of you, your family, your habits and other personal information. 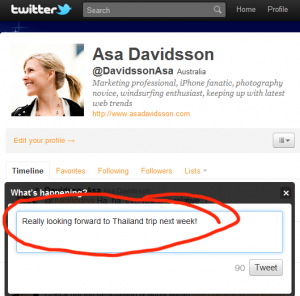
Software like Twitter and Foursquare are often used at conferences, parties and other social scenes where alcohol is consumed, increasing chances of personal and location information slipping out. Travel plans and experiences while on holiday is often communicated via Twitter, giving clue to others that you’re not at home, leaving your family or possessions at risk for intruders.
Your Foursquare check-ins to local restaurants and shops can also make it fairly simple to determine what area you live in and your habits. Something as innocent as a Foursquare airport check-in is a tell-tale sign you’ll be away from home for at least one night.
3. Search yourself
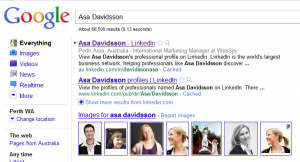 Sometimes referred to as vanity search, it is a very good idea to search your name on Google and check out your profile as others see it on social networking sites. Understand where you show up and what information is available about you, and then adjust your profile, settings and habits appropriately.
Sometimes referred to as vanity search, it is a very good idea to search your name on Google and check out your profile as others see it on social networking sites. Understand where you show up and what information is available about you, and then adjust your profile, settings and habits appropriately.
If you unexpectedly see your name in locations you don’t frequent, it could give you a heads up someone else is using your identity online. Set up a Google alert with your name. Google Alerts will email you weekly, daily or immediate notifications when the Google robots comes across your name online.
4. Setup an OpenID account
OpenID is an open source standard for creating a single sign-on to multiple online services and applications. With OpenID, your password is only given to your identity provider, and that provider then confirms your identity to the websites you visit. Other than your provider, no website ever sees your password, so you don’t need to worry about an unscrupulous or insecure website compromising your identity
As a framework, OpenID accounts are available from multiple providers. Companies like AOL, Microsoft, Sun, and Novell are beginning to accept and provide OpenIDs. It is estimated that there are over 160-million OpenID enabled URIs with nearly ten-thousand sites supporting OpenID logins.
OpenID is making inroads into the SaaS application market to better manage user accounts. We’re also likely to see OpenID used in online social networking sites to help verify users identities and reduce impersonators and false identities. If the social networking sites you frequent don’t use OpenID or a similar technology, e-mail the site creator and lobby for adding it.
5. Don’t violate your company’s social networking policies
As blogging and social networking sites enter the workplace corporate acceptable use policies (AUP) are being updated to define boundaries for employees, contractors and the company.
Data leakage incidents (loss of corporate, confidential or customer information), making inappropriate public statements about the company, using corporate resources for personal uses and harassing or inappropriate behavior toward another employee can all be grounds for reprimand or dismissal. Social networking sites are another way those things can happen and they create an easy digital paper trail to investigate.
Data leakage (or loss) prevention is currently one of the hottest areas in security. Companies are looking for ways to prevent company confidential and proprietary information from slipping through the firewall. Most incidents probably occur via email or file transfers but IM chat tools, blog posts, Twitter messages and even online resume content could disclose proprietary company information.
Even using social networking sites on company time or using company resources could be a violation of the company’s acceptable use policy. Before you become the corporate poster child for some publically humiliating episode from using social networks at work, check your corporate AUP to make sure you aren’t violating the policy.
Other Resources
http://www.microsoft.com/protect/parents/social/socialnet.aspx
http://www.networkworld.com/community/tips-for-safe-social-networking
See also:
- Security Threats Increase with Growth in Social Networking – Blocking still not the Answer
- U.S Army End Ban on Social Media Sites
- New Study Unveils – Employee Access to Internet more Important than Salary or Title
- Latest Research and 5 Tips for Managing Web 2.0 in the Workplace
- The Cost of Blocking Employee Internet Usage

Leave A Comment